
Malicious URL Example: Types of Malicious Sites We Catch
Not all malicious websites use the same template. While the term “malicious site” might conjure up an image of a dozen pop-up ads, flashing red alerts, or a window saying “AlL FiLeS ArE BeLoNg To Us”. You’re not totally wrong to imagine those things, though you’re missing a lot of malicious URL categories if that’s all you can think of when it comes to cyber threats.
In this blog, I’m going to discuss the types of malicious URL categories Webshrinker looks for with actual examples of what it’s caught.
Webshrinker’s malicious URL categories
Webshrinker’s ability to categorize sites as malicious is technically separate from its ability to categorize “normal” sites. Before Webshrinker determines the category of a site, it first does a variety of checks to see if the site is malicious before giving it a category such as “gambling.” Because of this, if a site turns out to be malicious, that site will only be assigned a “deceptive” value and won’t be categorized like a non-malicious site.
For a quick overview of the types of malicious categories Webshrinker can find, here’s a list of what it typically looks for:
- Botnet: These are Command and Control botnet hosts. Blocking these sites prevent you from receiving commands from already-infected machines.
- Cryptomining: Sites which server files or host applications that force your web browser to mine cryptocurrency. This can use a lot of resources.
- Malware: Malware is a parent category for a lot of different types of malicious software including ransomware, viruses, spyware, and trojans.
- Phishing scams: Websites with a goal of tricking you into handing over personal data. (We have a great blog about phishing on our parent company’s site).
These are broad categories, but it gives you an idea of the range of malicious sites Webshrinker searches for.
But now let’s focus on actual examples of malicious URLs that fit into these categories. Not all phishing sites look identical. Additionally, sites carrying malware vary significantly from scam to scam. We’ll hold up the magnifying glass to a few of them here.
If you find malicious URL examples like this fascinating, make sure you follow us on Twitter for our weekly #PhishingFriday updates!
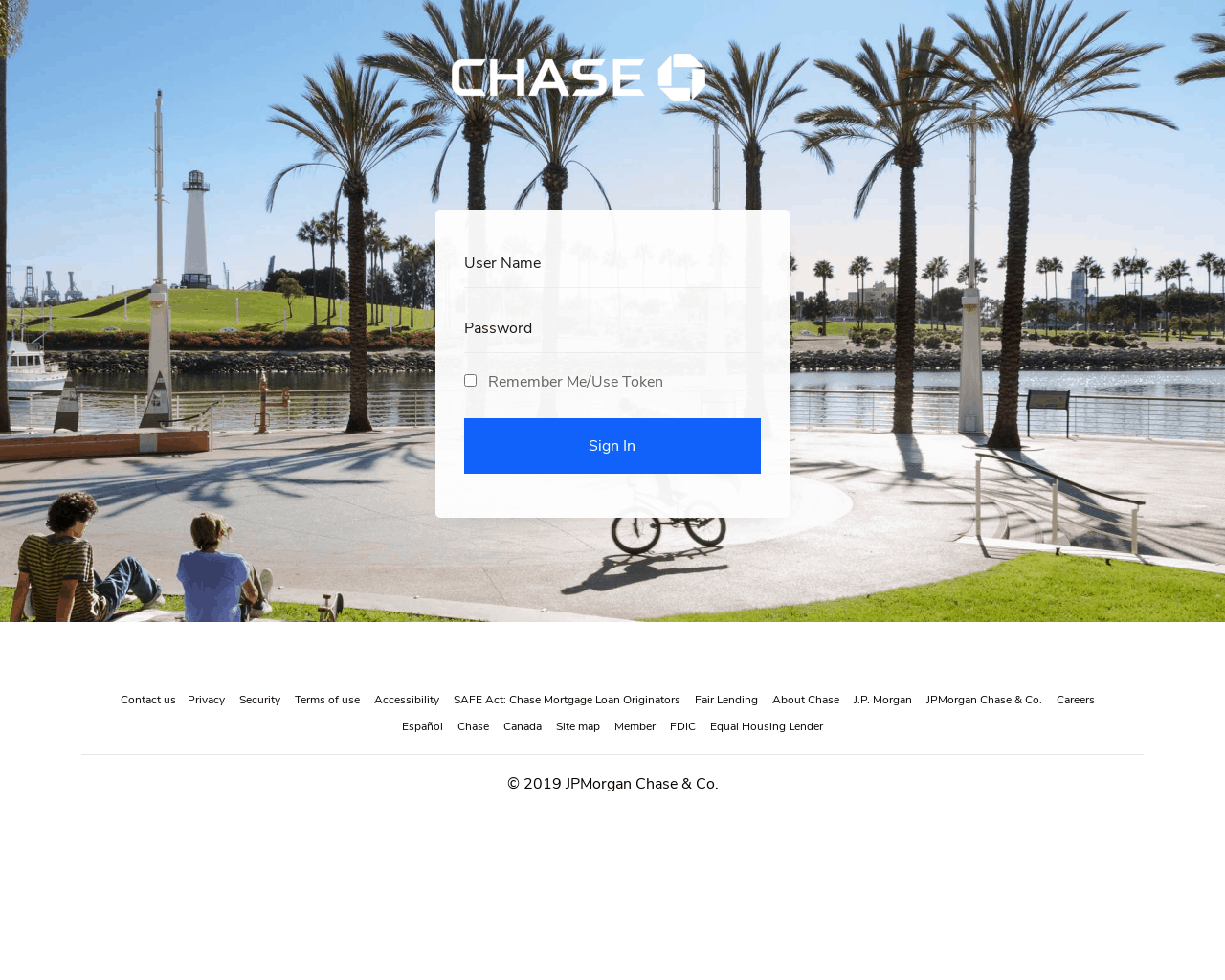
Lookalike domains
Lookalike domains are a growing problem, but they’re nothing new. The idea behind these is simple: Mimic the login page of a big, trustworthy company like Netflix, Paypal, or Bank of America and ask someone to login.
Sometimes the goal is simply to access that account. Banks and Paypal are a great example. Once they have your info, they can redirect you to the real website and you’d never know. This is called a “man-in-the-middle attack.”
However, sometimes they’ll ask you to enter your credit card information.
So how do they do it? Well, first, the URL needs to be similar enough to the original. Or needs to be what looks like a convincing subdomain. For instance, Facebook uses a lot of subdomains that you’re probably familiar with as well as its own link shortener (fb.me). Seeing something similar in your address bar doesn’t necessarily throw any red flags. However, domain categorization will be able track this.
But a good phony domain is nothing without good design. Here are a few examples that we’ve found.
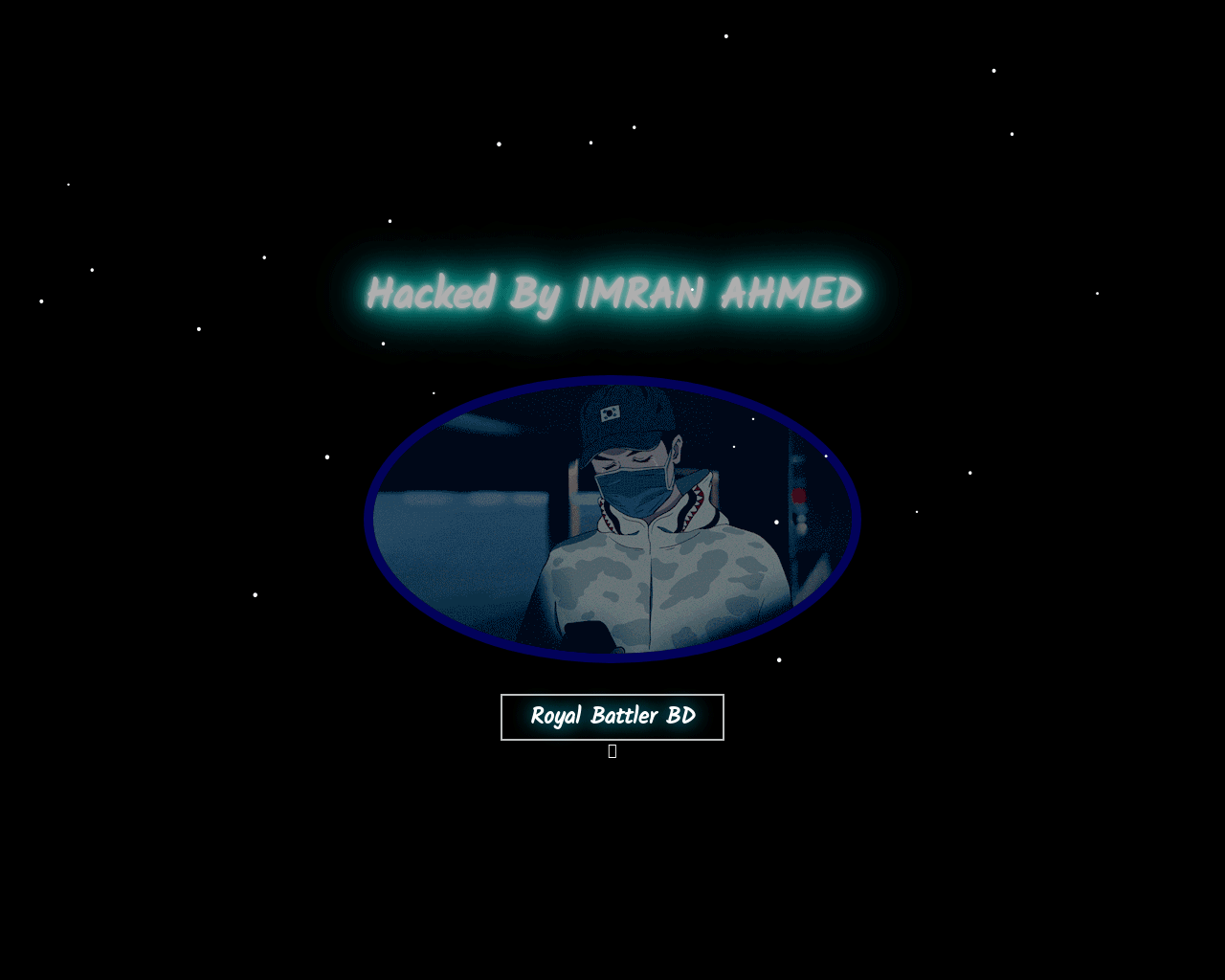
Compromised domains
Hackers like attention. When they exploit a vulnerability in a website, they like to leave their autograph behind. Sometimes these compromised sites carry malware, and sometimes they serve as a warning. They might also be holding the site for ransom.
WordPress sites are particularly vulnerable to hackers, as when plugins become outdated it can create a weakness that can then be penetrated. This is why it’s really important for WordPress maintainers to keep plugins current.
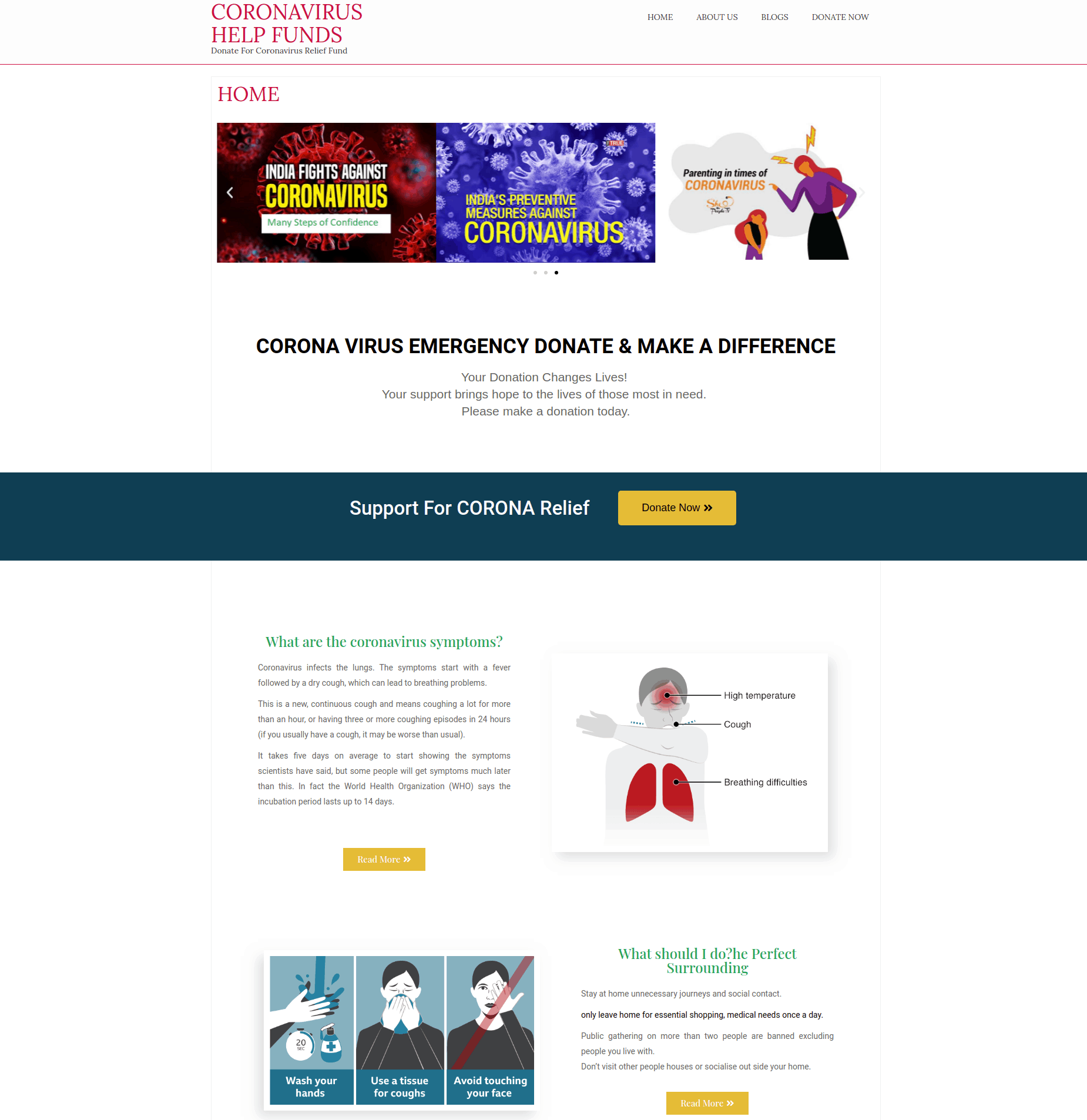
Charitable scams
These types of phishing sites are very similar to the lookalike domains. However, they’re not necessarily trying to look like any sites you might be aware of. Instead, what they’re attempting to do is trick you into donating to them. With the coronavirus pandemic, we’ve seen a huge uptick in coronavirus-related charitable scams.
Unfinished pages
Despite often wanting all of the credit and signing their name to their attacks, some hackers are just lazy. One sign that a site is malicious is when it’s incomplete. The top part of the website (above the fold) will look like a legitimate site, while the rest of it will just be a template. Usually when you click around the site, you’ll find that either the other links don’t bring you anywhere or the content is missing.
These sites can carry malware, or they can be phishing scams trying to convince you on that sloppily-crafted homepage to enter your credit card information.

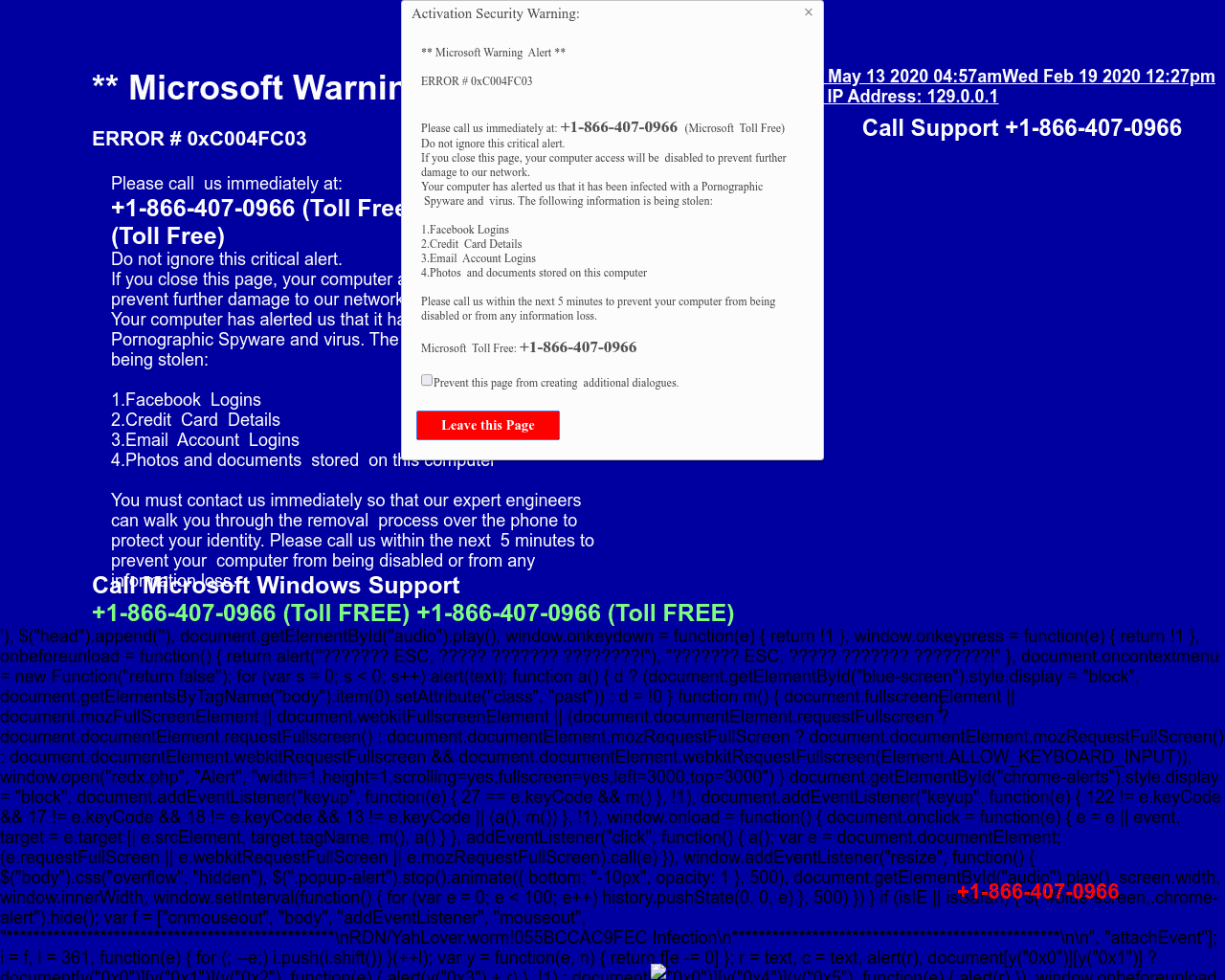
Pop-up scams
Remember that flashing red warning sign I mentioned earlier? There are still some sites that try it. At least, they pay an homage.
These ransomware-inspired phishing sites claim that your computer has experienced a vulnerability and you need to act quickly. There’s usually a phone number you can call to talk to support (usually pretending to be Microsoft) or even a button to click where you can enter your credit card information. The price is sometimes small, but these hackers are potentially attempting to steal your credit card. They won’t be placated by a $20 payout.
If you see a webpage claiming to be Microsoft alerting you to some sort of scam, navigate away.
Are you looking to add malicious URL detection to your application? Sign up for a free trial of Webshrinker.
We curate our sets of categories very carefully, and only update them after thorough consideration. Here are the newest Webshrinker categories.
read more
